Introduction
The world has never been more connected than it is today. The Internet has become critical to our everyday lives, for businesses and individuals, and so too has its security. With our growing dependence on networked digital systems comes an increase in the variety and scale of threats and cyber attacks.
A variety in the protective methods used by countries or organizations can make it difficult to assess risk systematically and to ensure consistent, adequate security.
Therefore, standards have a key role to play in improving cybersecurity – protecting the Internet, its communications and the businesses that rely on it – and TC CYBER is the most security-focused technical committee in ETSI.
Our Role & Activities
TC CYBER is recognized as a major trusted centre of expertise offering market-driven cyber security standardization solutions, advice and guidance to users, manufacturers, network, infrastructure and service operators and regulators. ETSI TC CYBER works closely with stakeholders to develop standards that increase privacy and security for organizations and citizens across Europe and worldwide. We provide standards that are applicable across different domains, for the security of infrastructures, devices, services, protocols, and to create security tools and techniques. Look at the TC CYBER Road map below for more details.
The Quantum-Safe Cryptography working group is a subgroup of TC CYBER; you can find out more about their work.
In addition to TC CYBER, other ![]() ETSI groups also work on standards for cross-domain cybersecurity, the security of infrastructures, devices, services and protocols and security tools and techniques. They address the following areas and more information can be found in the related technologies pages:
ETSI groups also work on standards for cross-domain cybersecurity, the security of infrastructures, devices, services and protocols and security tools and techniques. They address the following areas and more information can be found in the related technologies pages:
- Cross-domain cybersecurity
- Information Security Indicators
- Encrypted traffic integration
- Securing technologies and systems
- Mobile/Wireless systems (5G, TETRA, DECT, RRS, RFID...)
- IoT and Machine-to-Machine (M2M)
- Network Functions Virtualisation
- Intelligent Transport Systems, Maritime
- Broadcasting
- Securing Artificial Intelligence
- Security tools and techniques
- Lawful Interception and Retained Data
- Digital Signatures and trust service providers
- Secure elements
- Security algorithms
Take a look at ETSI’s annual Security Week event for more on the work of ETSI in cybersecurity or watch the video from our security week:
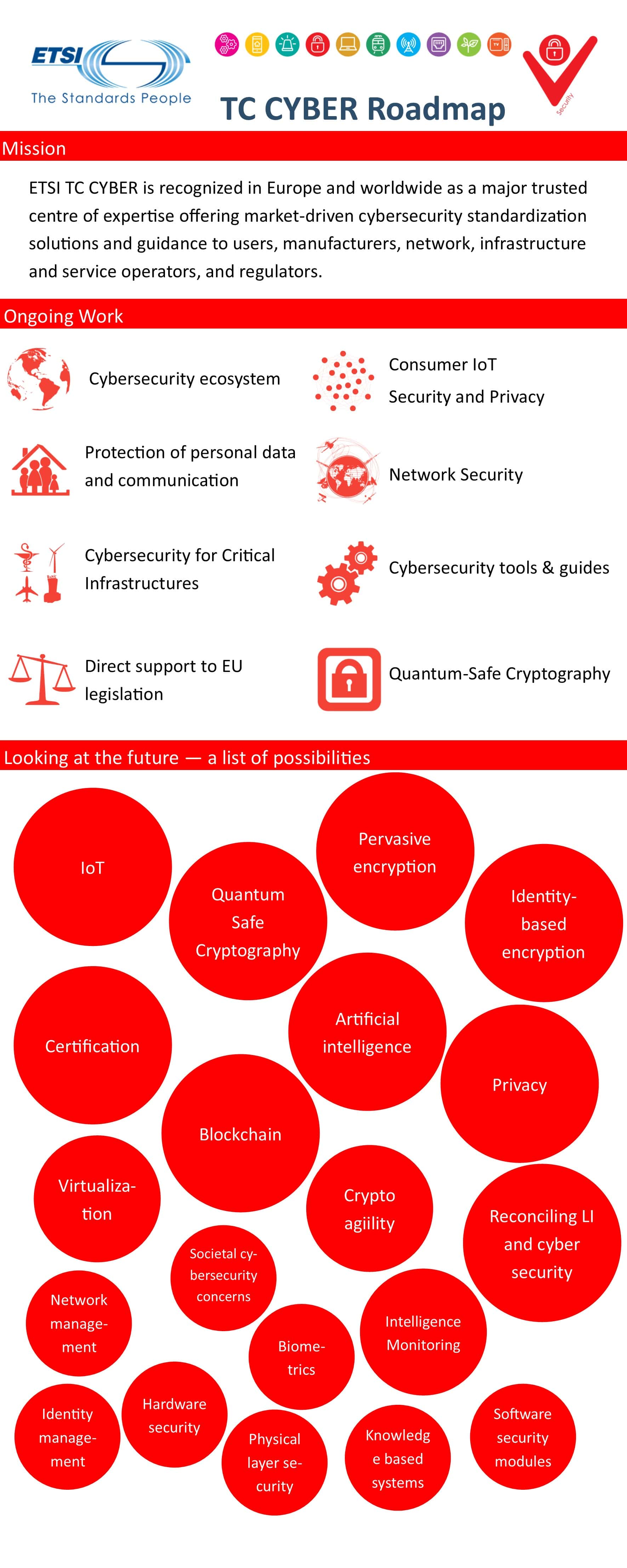
TC CYBER Road Map
See the details of the CYBER Road Map.
Consumer IoT security
See the details of the Consumer IoT security Road Map.
Standards
A full list of related standards in the public domain is accessible via the CYBER committee page.