A recent study at ETSI ZSM addresses potential security threats to zero-touch network and service automation
Zero-touch network and service automation are essential to unleash the business potential of 5G and beyond. The ultimate automation target is a largely autonomous operation driven by high-level policies and rules, enabling self-configuration, self-monitoring, self-healing and self-optimization – without further human intervention.
Automation is not only about technology; it also requires changes in the mindset of people. Trust is a major barrier to adoption and striving to build it requires a continuous learning process. As more automation processes are deployed and operate safely and efficiently, human trust will increase and the requirement for a level of supervision/intervention will diminish. Having native security (e.g. an adaptive secured framework, access control, trustworthiness, data protection) can help to establish confidence and instill trust as the automated processes deliver the intended business outcomes.
The threat surface in the ZSM environment is extensive, firstly due to the openness of the ZSM framework. The framework is modular, extensible and service-based and expands across multiple domains. Its interfaces are open and offer model-driven services. Protecting the interfaces and the management services within and across the domains is essential to ensure the trustworthiness of the ZSM framework.
In addition, the ZSM services can be produced and consumed by new players coming from diverse industries (e.g. government, vehicle industry, energy, transport, etc.). Each player may require or support different trust levels according to its own deployment/execution environments, security policies and regulations. This variety demands flexible and adaptive security control.
Furthermore, the ZSM framework enables adaptive, closed-loop automation, leveraging emerging technologies, such as AI/ML, data lake, cloud-native applications, intent-based management, etc. These underlying technologies introduce new vulnerabilities to attacks and impose additional security requirements. For example, it is necessary to ensure trustworthiness and guard the AI and ML algorithms from highly sophisticated, creative and malicious attacks, including abuse, trolls, data poisoning, and model rescue. Moreover, it is critical to protect data, ensuring its integrity, confidentiality and availability as well as preserving privacy to comply with security laws and regulations. At the same time, the ZSM framework can take advantage of these emerging technologies to increase the security management efficiency. For example, using AI/ML-empowered analytics to trigger actions can help to automate security monitoring and the real-time response to incidents (e.g. the fast deployment of new security functions in the cloudified environment).
The recently released ZSM report (ETSI GR ZSM 010) presents a comprehensive and extensive study that was conducted by the ZSM group on the security aspects relating to the ZSM framework and solutions. The study leverages well-established methodologies to identify and analyze the potential security threats and assess the related risk scores and priorities. The report proposes mitigation options, countermeasures and security controls to address the threats and risks to the ZSM framework and solutions.
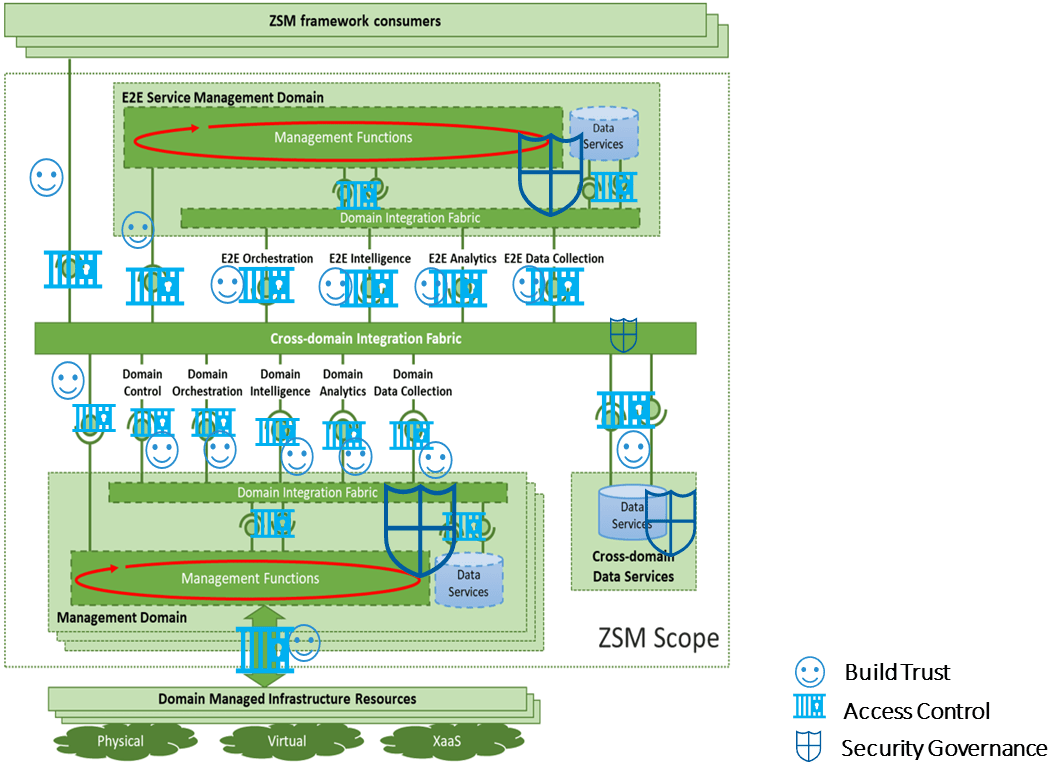
Figure 1 below illustrates the required security countermeasures and control of the ZSM framework.
Figure 1: Security countermeasures and control of the ZSM framework
The ZSM security risks and threats need to be continuously analyzed and mitigated. The ultimate goal is to build a native, adaptive security framework to automate the security processes, capable of predicting threats, detecting attacks and analyzing and mitigating risks – without further human intervention. AI/ML may be used to empower such cyber-defense.
ZSM security is transversal and should be considered for the design phases of the ZSM work. The capabilities of the ZSM framework and its security properties can be leveraged to build intelligent and autonomous security services which will protect the ZSM managed services. The normative work on ZSM security aspects (ETSI GS ZSM 014) has commenced. The aim is to specify capabilities and services to ensure a secured and trusted ZSM framework and solutions and to automate security processes for managed services.
The ETSI ISG ZSM is open to ETSI members and non-ETSI members. Industry players and technologists who care about automation and security are welcome to join the group and assist with the development of state-of-the-art security solutions for the zero-touch network and service automation and help to accelerate their adoption.